Rail-fence Cipher
Introduction §
The railfence cipher is a very simple, easy to crack cipher. It is a transposition cipher that follows a simple rule for mixing up the characters in the plaintext to form the ciphertext. The railfence cipher offers essentially no communication security, and it will be shown that it can be easily broken even by hand.
Although weak on its own, it can be combined with other ciphers, such as a substitution cipher, the combination of which is more difficult to break than either cipher on it's own.
Many websites claim that the rail-fence cipher is a simpler "write down the columns, read along the rows" cipher. This is equivalent to using an un-keyed columnar transposition cipher.
Example §
The key for the railfence cipher is just the number of rails
. To encrypt a piece of text, e.g.
defend the east wall of the castle
We write it out in a special way on a number of rails
(the key here is 3)
d . . . n . . . e . . . t . . . l . . . h . . . s . . . . e . e . d . h . e . s . w . l . o . t . e . a . t . e . . f . . . t . . . a . . . a . . . f . . . c . . . l .
The ciphertext is read off along the rows:
dnetlhseedheswloteateftaafcl
With a key of 4:
d . . . . . t . . . . . t . . . . . f . . . . . s . . . . e . . . d . h . . . s . w . . . o . t . . . a . t . . . . f . n . . . e . a . . . a . l . . . h . c . . . l . . . . e . . . . . e . . . . . l . . . . . e . . . . . e
The ciphertext is again read off along the rows:
dttfsedhswotatfneaalhcleelee
JavaScript Example §
This is a JavaScript implementation of the Railfence Cipher.
Plaintextkey =
Ciphertext
Cryptanalysis §
Cryptanalysis is the art of breaking codes and ciphers. The railfence cipher is a very easy cipher to break. A cryptanalyst (code breaker) simply has to try several keys until the correct one is found. It is very easy to find a key if you know some of the plaintext, or can guess some of it. Anagramming is another very powerful method that can be used with any transposition cipher, that consists of taking chunks of ciphertext and guessing what the plaintext would be.
A peculiarity of transposition ciphers is that the frequency distribution of the characters will be identical to that of natural text (since no substitutions have been performed, it is just the order that has been mixed up). In other words it should look just like this:
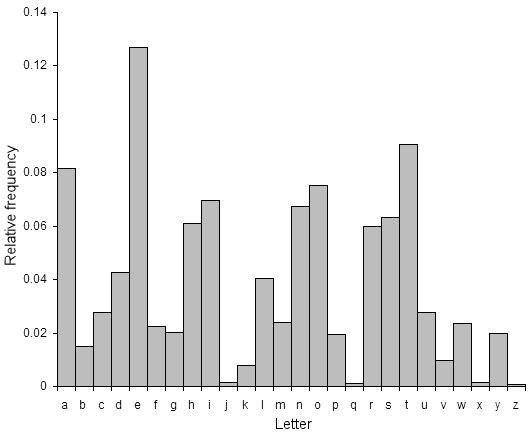
For a method that works well on computers, we need a way of figuring out which of the keys results in the most english like plaintext after decryption. For automated methods of determining how 'english like' a piece of text is, check out the Classical Cryptanalysis section, in particular Quadgrams as a fitness measure. The key that results in a decryption with the highest likelyhood of being english text is most probably the correct key. Of course, the more ciphertext you have, the more likely this is to be true (this is the case for all statistical measures, including the frequency approaches above). So the method used is to take the ciphertext, try decrypting it with each key, then see which decryption looks the best. This simplistic method of cryptanalysis (checking every single possible key) only works on very simple ciphers such as this cipher, even slightly more complex ciphers can have far too many keys to check all of them.
References §
- Wikipedia has a good description of the encryption/decryption process, history and cryptanalysis of this algorithm
- Simon Singh's 'The Code Book' is an excellent introduction to ciphers and codes.
- Singh, Simon (2000). The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography. ISBN 0-385-49532-3.
Further reading
We recommend these books if you're interested in finding out more.
 The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography
ASIN/ISBN: 978-1857028799
Simon Singh's 'The Code Book' is an excellent introduction to ciphers and codes
Buy from Amazon.com
The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography
ASIN/ISBN: 978-1857028799
Simon Singh's 'The Code Book' is an excellent introduction to ciphers and codes
Buy from Amazon.com

